Home & Global Resources
Blueprint Assess
Blueprint Migrate
Getting Started
The Blueprint User Interface
Change Your Password
Open a Project
Organize Artifacts and Assets
Close a Project
Status Indicators
Jobs
Exporting from Source RPA Tools
How to export a UiPath Automation Project from UiPath Orchestrator
How to export .bprelease files from Blue Prism
Blue Prism VBO Matching on Import
How to Export .zip files from Automation A360 Control Room
Importing
Exporting
RPA Export from Blueprint
Variable Prefixing
Why We Create Multiple Similar Subflows During Migration
Understanding Wrapper Subflows in Power Automate Desktop
Setting up defaultRunDotNetScriptReferences
AsEnumerable Support
XmlDocument Support
Bulk Reimport/Recalculate
Metabot Migration - Best Practices
Exporting Blue Prism VBO
Artifacts Management
Base Artifact Types
Creating and Managing Artifacts
View and Edit Artifacts in the Utility Panel
Concurrent User Activity in Artifacts (Steal Lock)
Using Descendants View
Global Actions
Rules
Rules Overview
Rule Pre-Requisites
Using Rules
Rules User Interfaces
Using the Rules Table
Using Rules CSV
Using the Rules Wizard
Custom Action Mapping
Reuse Mapping to Power Automate Desktop
Manual Reuse
TODO, Error, and Robin Mapping
Script Mapping
Variable Name Dependency Mapping
Variable Renaming and Initialization
DLL/Method Invocation Mapping
Unresolved References
Work Queues Mapping
Solutions & Best Practices
Working with Migration Output in Power Automate Desktop (PAD)
Blueprism to PAD Migration Output Details
UiPath to PAD Migration Output Details
A360 to PAD Migration Output Details
RPA Value-Mapping Assessments
Why Choose Blueprint Cloud vs. On Premise ?
Setting up SAP for RPA
UiPath Conversion of "Sharepoint Scope and Get File"
API & Developer Resources
REST API Request Header and Parameters
REST API Request Body and Parameters
REST API - Listing Artifacts in the Request Body
REST API - Defining an Artifact in the Request Body
REST API - Defining a Comment in the Request Body
REST API - Defining a Reply in the Request Body
REST API - Defining a Trace in the Request Body
REST API - Filter Parameter
REST API - Defining a User in the Request Body
REST API Requests
REST API - Add Attachment to Subartifact Request
REST API - Get Artifact Request
REST API - Add Traces Request
REST API - Get Project by Id Request
REST API - Update Custom Choice-Property Type Request
REST API - Publish Comments Request
REST API - Publish Artifact Request
REST API - Update Comment Request
REST API - Delete User Request
REST API - Add Comment Request
REST API - Close Review Request
REST API - Get Discussion Status Request
REST API - Update Reply Request
REST API - Get Attachment Request
REST API - Delete Comment Request
REST API - Create Project Request
REST API - Get Group Request
REST API - Rate Comment Request
REST API - Get Child Artifacts of Artifact Request
REST API - Discard Artifacts Request
REST API - List Artifacts Request
REST API - Rate Reply Request
REST API - Move Artifact Request
REST API - Delete Attachment Request
REST API - List Projects Request
REST API - Get Blueprint Product Version Request
REST API - Update Standard Choice Property Request
REST API - Get Review Request
REST API - Reply to Comment Request
REST API - Update User Request
REST API - Get Collection Request
REST API - Delete Artifact Request
REST API - List Collections Request
REST API - Authenticate Request
REST API - Get Artifact Type Request
REST API - List Artifact Types Request
REST API - Delete Reply Request
REST API - Get Root Artifacts of Project Request
REST API - Add Attachment Request
REST API - Create User Request
REST API - List Reviews Request
REST API - List Groups Request
REST API - Get User Request
REST API - Delete Traces Request
REST API - Add Artifact Request
REST API - List Users Request
REST API - Get Artifact Image Request
REST API - Update Artifacts Request
REST API - List Unpublished Artifacts Request
REST API HTTP Methods
REST API - HTTP HEAD Method
REST API - HTTP DELETE Method
REST API - HTTP GET Method
REST API - HTTP POST Method
REST API HTTP Status Codes
REST API - HTTP PATCH Method
Blueprint REST API
REST API Quick Start Example
REST API Requests and Responses
REST API Security and Authentication
REST API Known Issues & Constraints
REST API Requests
REST API Resources
REST API - Defining an ALM Job in the Request Body
Dashboards & Reports
Statistics Report Options
Using Scope and View
Statistics Dashboard
Statistics Reports
Applications Dashboard
Applications Report
Estimator Dashboard
Estimator Reports
How to Change the Main Process Label for Estimations
Bulk Reporting
Call Trees
Blueprint + PowerBI Dashboards
How to Create Microsoft Power Automate RPA Migration Estimates with Blueprint
Licensing
Settings & Administration
Overview of Blueprint Settings
System Reports
System Reports
License and Activity Reporting
User List
Project Activity
User Roles
Artifact Map
Project Usage
User Activity Report
Audit Log
System Logs
User Management
Creating and Managing Users
Creating and Managing Groups
Creating and Managing Instance Administrator Roles
Creating and Managing Project Administrator Roles
RPA Management
Microsoft 365 Authentication Settings
Integration Reporting
Migrate - Import/Export
Migrate - Dashboards
Migrate
Analyze
Automation360 Authentication Settings
GenAI
Advanced Settings
Projects
Installation
Blueprint Installation Guide
System Requirements
Supported Third-Party Components
Azure App Registration (Power Automate Export)
Release Notes
Table of Contents
- All Categories
- Blueprint Assess
- Getting Started
- Dataverse Service Account Secret Setup
Dataverse Service Account Secret Setup
This article guides administrators through configuring a Service Principal in Azure AD and Dataverse to enable Blueprint Analyze to import desktop flow data. It covers setting up a custom security role with necessary table permissions, creating an application user tied to your PAD Export Azure AD app, and securely storing the client secret in Blueprint’s RPA Management settings. Once completed, Blueprint can synchronize and analyze flow runs and traces across your specified Dataverse environment.
IMPORTANT Pre-Requisites:
2. Your Dataverse environment must have action-log uploads enabled (default on).
3. Each desktop flow run supports up to 32 MB of action logs (~50K–80K entries). Split long flows if you exceed this limit.
4. A Service Principal/Account with a custom security role is required to read the following tables for all desktop flows:
- flowsession
- process (workflow)
- desktopflowbinary
- systemuser
For details on registering your Azure AD app, see Azure App Registration (Power Automate Export).
Analyze imports flowsession data (flow runs and traces) across your Dataverse environment by leveraging a Service Principal with a custom security role that grants Organization-level read access to the flowsession table. That role must also include read permissions on the process (workflow), desktopflowbinary, and systemuser tables. The Service Principal connects to the Dataverse environment specified in your PAD Export instance settings.
Create Power Platform Role
- In the Power Platform Admin Center, select the target environment (configured in Blueprint PAD export)
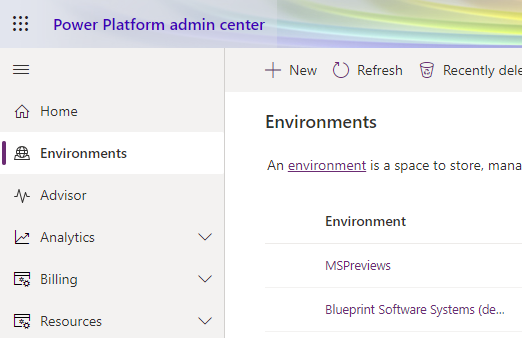
- Select Settings in the Toolbar
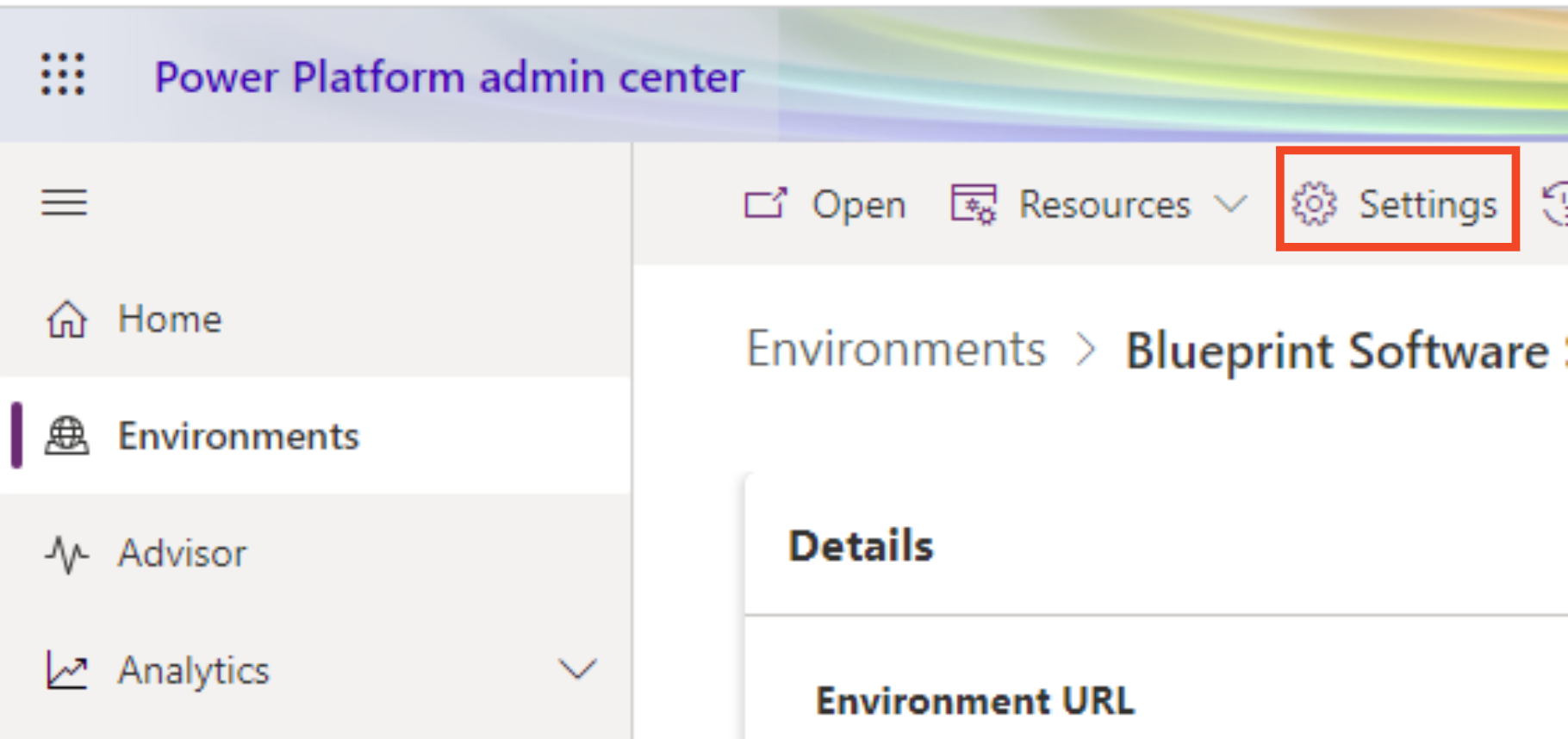
- Navigate to User + Permissions -> Security Roles
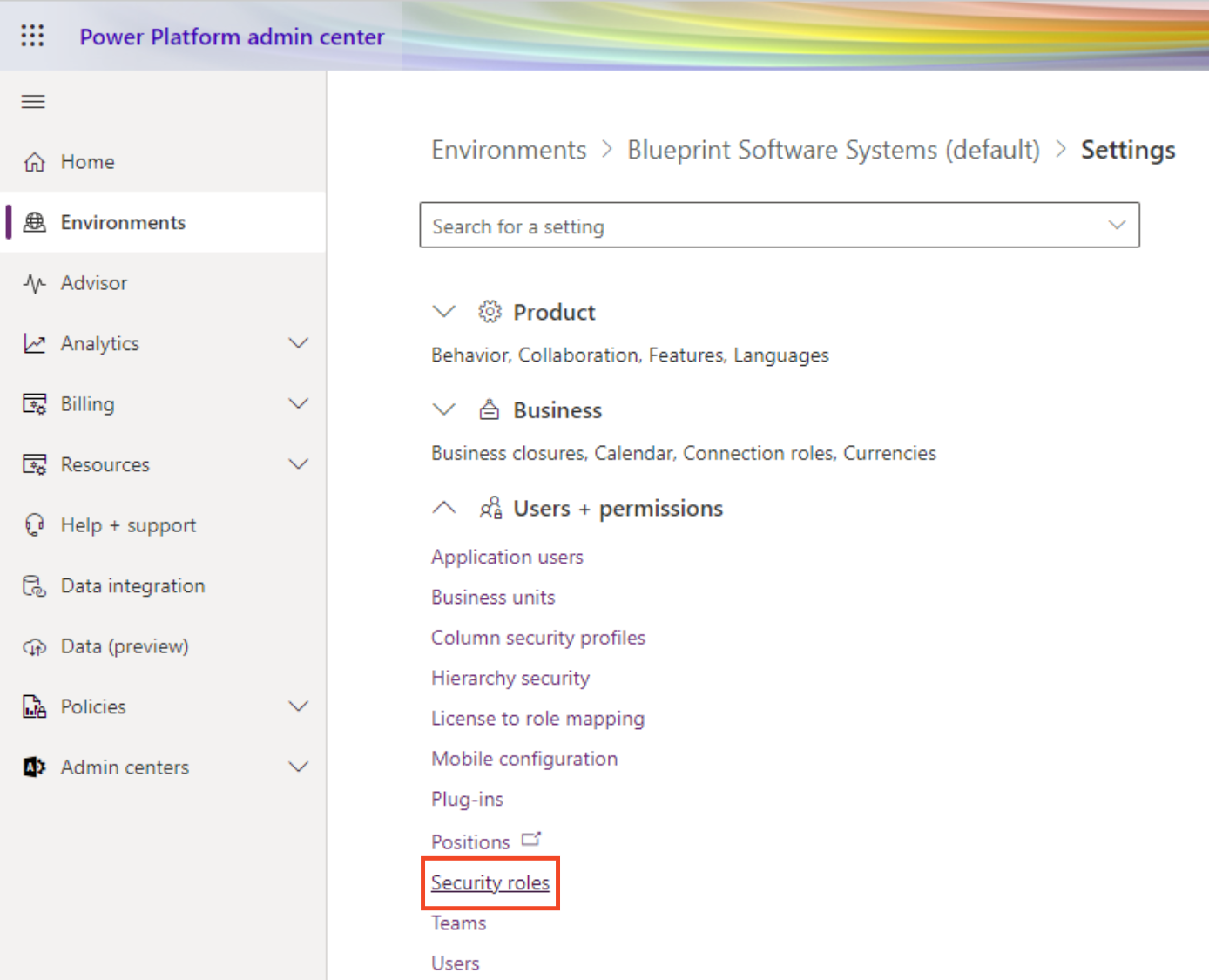
- Click New Role in the toolbar
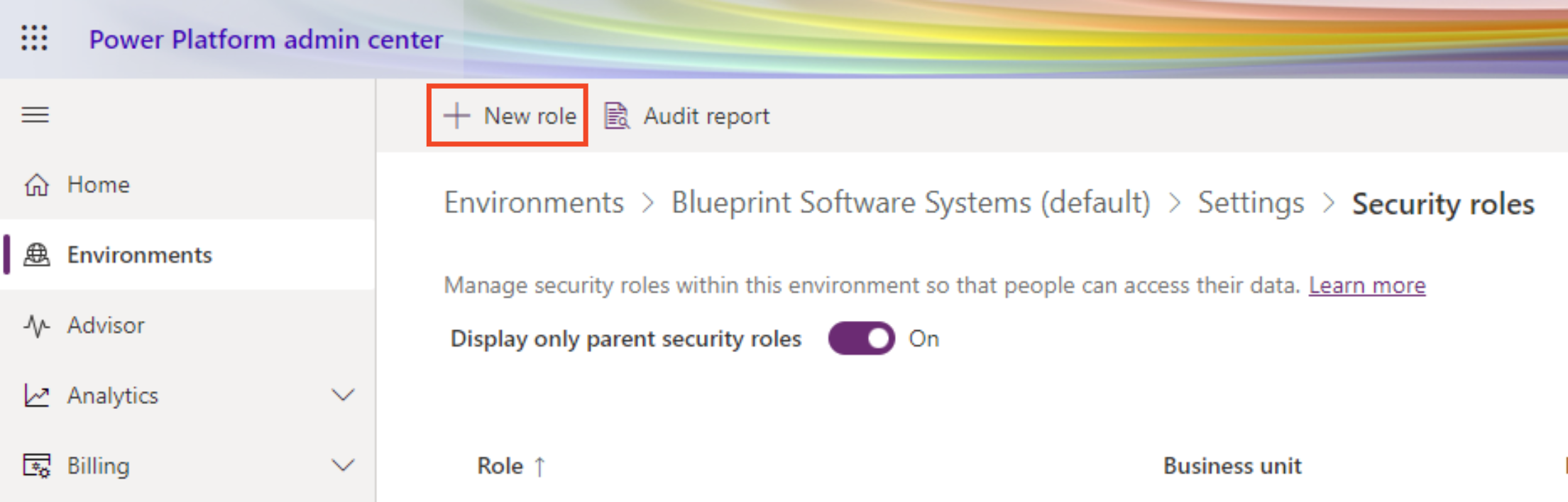
- Create new role, update, and Save
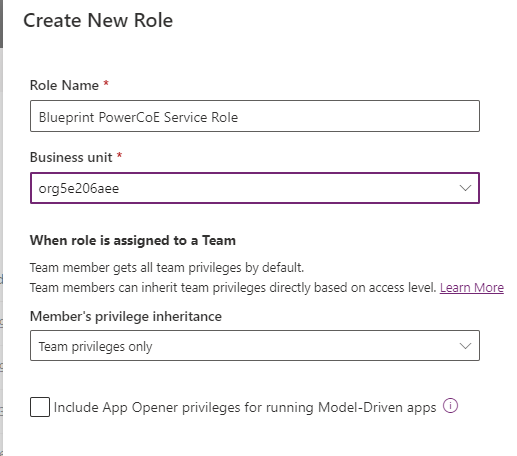
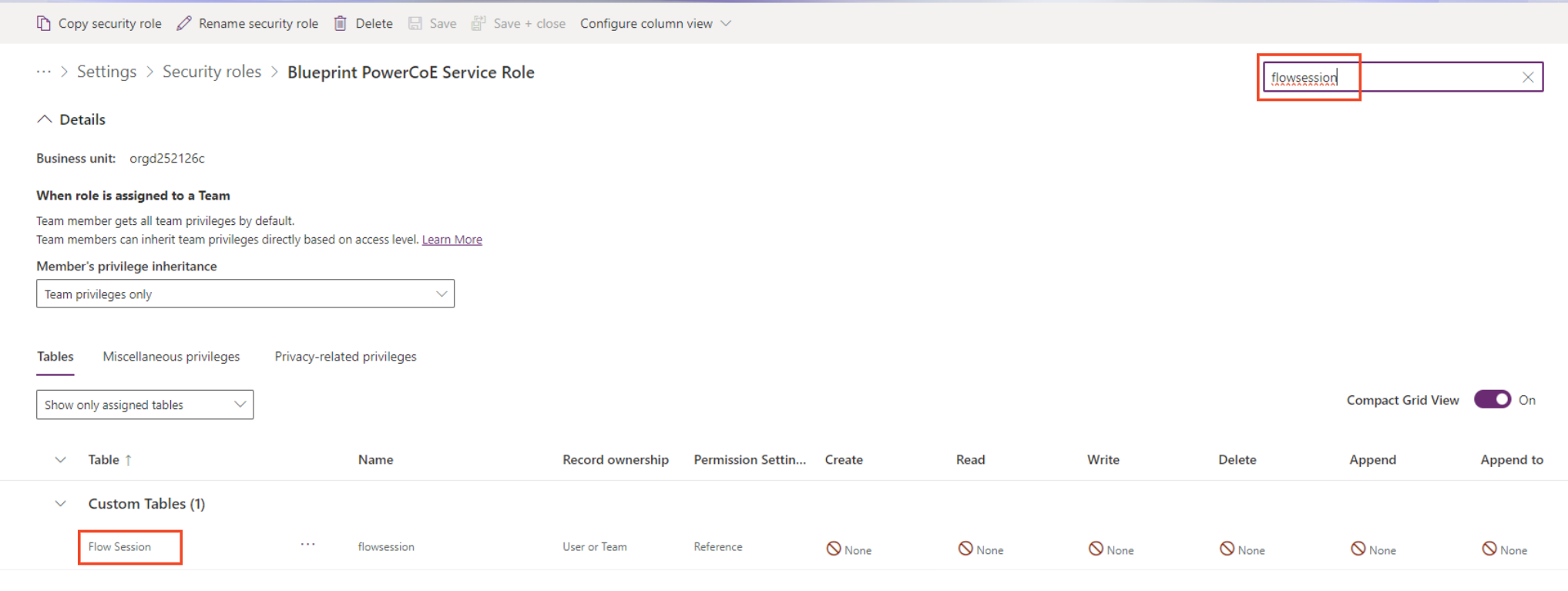
- Select Show All Tables (in the tables filter) and search for flowsession
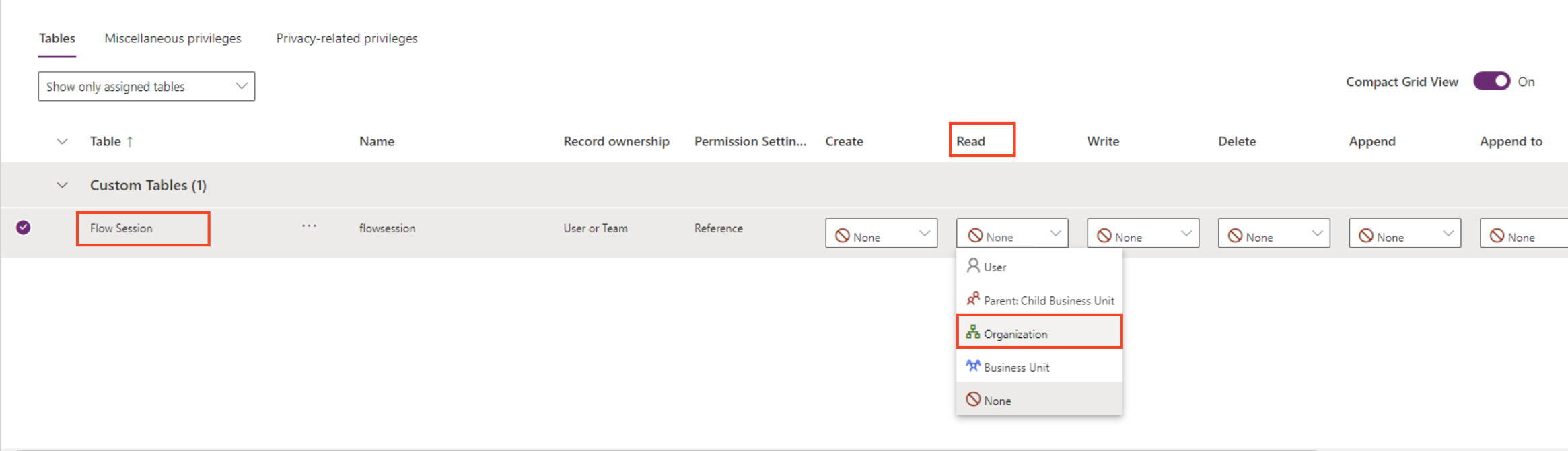
- Click on None value in the Read column for Flow Session row (Custom Table) and select Organization in the dropdown
- Search for process (workflow) table and change Read column permission to Organization
- Search for desktopflowbinary table and change Read column permission to Organization
- Search for systemuser table and change Read column permission to Organization
- Click Save and Close in the toolbar
Create Application User
- In the same environment settings, navigate to Users + Permissions -> Application Users
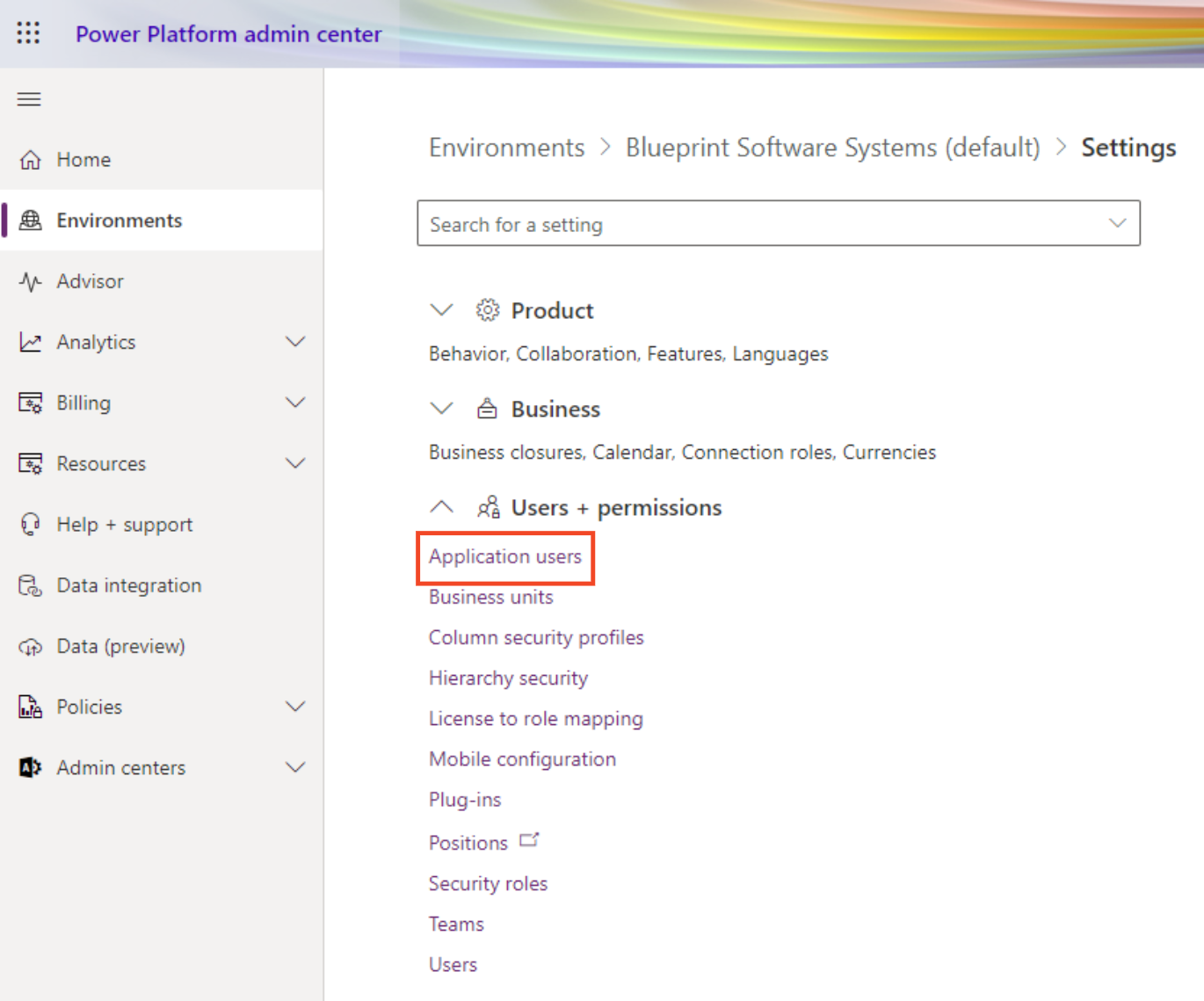
- Click New App User (add application user) and then Add an App
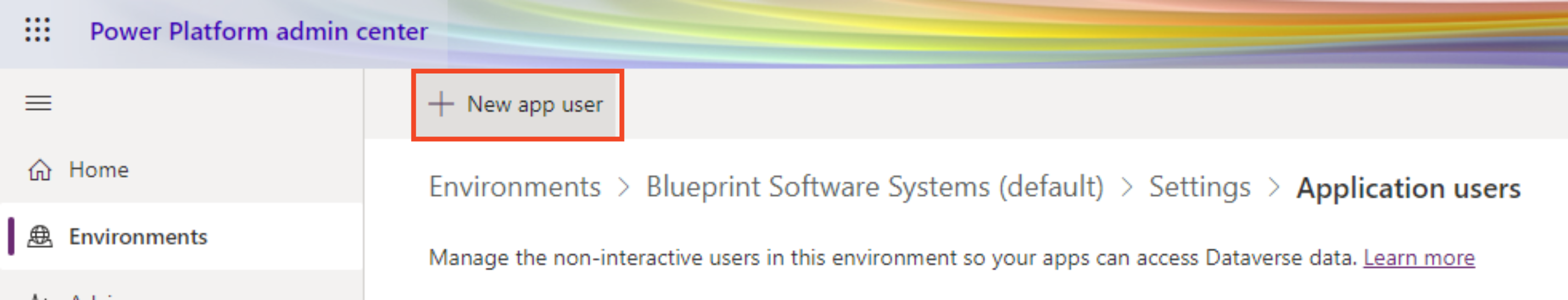
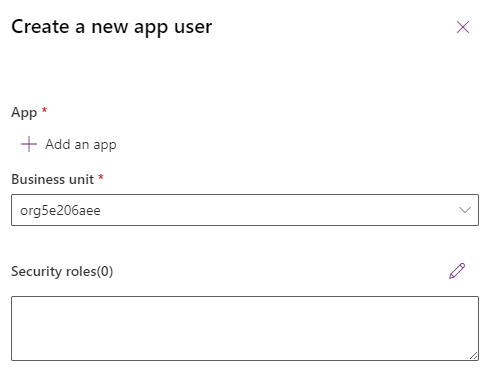
- Search for and select your pre-registered PAD Export Azure AD app and click Add
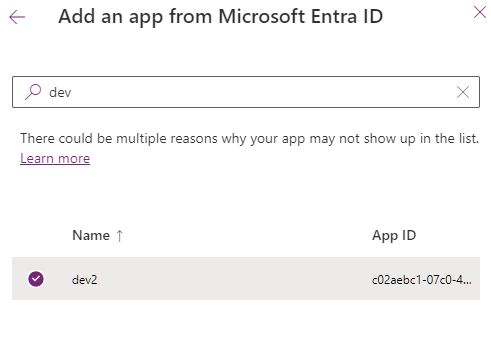

- Click on Security Roles (pencil icon) and select role created in the first section. Click Save
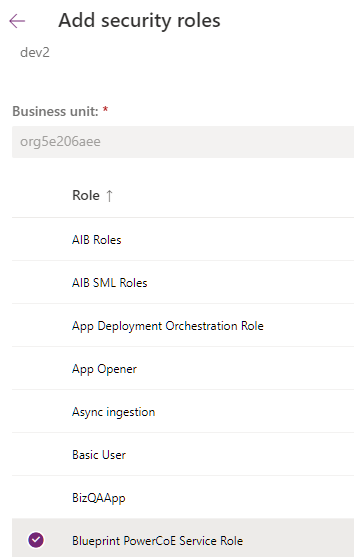
- Click Create
Generate and Set Service Account Secret
- In Azure AD, open your PAD Export app and create a New Client Secret
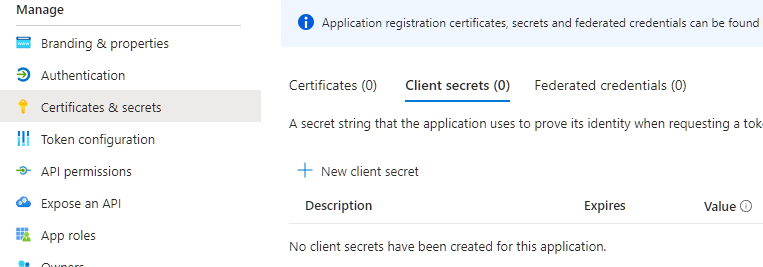
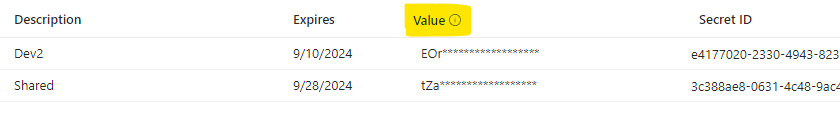
- Copy the Value of the generated secret (not the secret ID)
- In Blueprint, go to Settings -> RPA Management -> Analyze, enable Dataverse Synchronization, and paste the Value (not the secret ID) into the Service Account Secret field
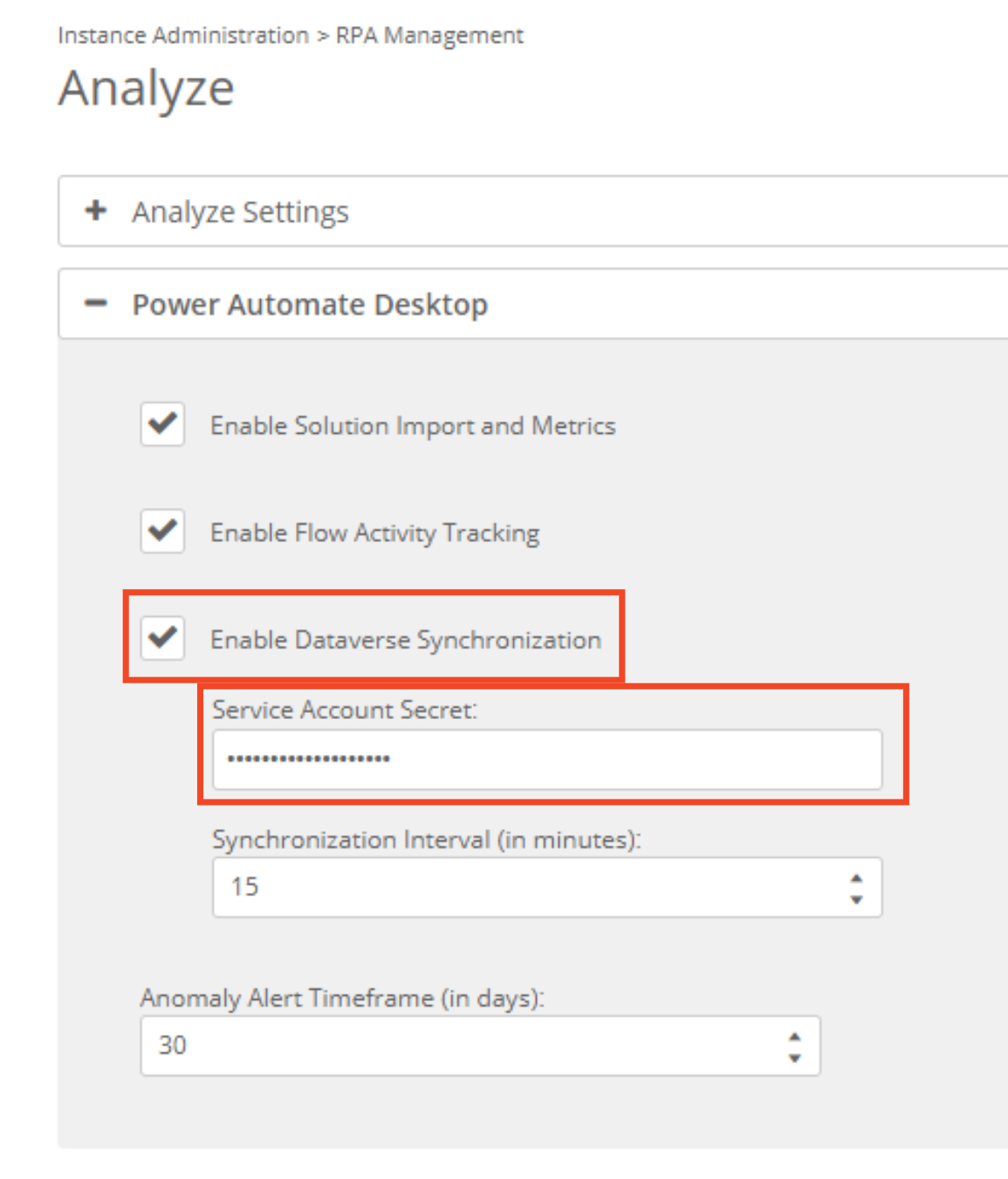
- Click Save
Your service account is now configured for Dataverse-based flow imports.
How did we do?
RPA Data Import
